Restricting SSH access to specific IPs is a fundamental security practice that limits who can access your server, helping reduce the risk of unauthorized access.
Prerequisites #
- Sudo SSH access to the server; either with user root or sudo user.
On Linux systems, you can use the hosts.allow and hosts.deny files to control access to SSH and other services.
Understanding hosts.allow and hosts.deny #
The hosts.allow and hosts.deny files are part of TCP Wrappers, a mechanism for filtering incoming connections based on predefined rules. You can specify which IP addresses are allowed or denied access to specific services by configuring these files.
/etc/hosts.allow: Specifies which IP addresses can access certain services./etc/hosts.deny: Denies access from IP addresses to services not allowed inhosts.allow.
Note: TCP Wrappers may not be enabled by default on all systems, so verify compatibility on your Linux distribution.
Step 1: SSH to your server. You can refer to this guide.
Step 2: Open hosts.allow and hosts.deny
- To start restricting SSH access, edit the configuration files. You can use vi or nano based on your preference.
sudo vi /etc/hosts.allow
sudo vi /etc/hosts.denyConfigure hosts.allow
- Access the
/etc/hosts.allowfile
sudo vi /etc/hosts.allow- Specify the allowed IP addresses. For SSH, add the following line, replacing
192.168.1.100with the IP address you wish to allow:
sshd: 192.168.1.100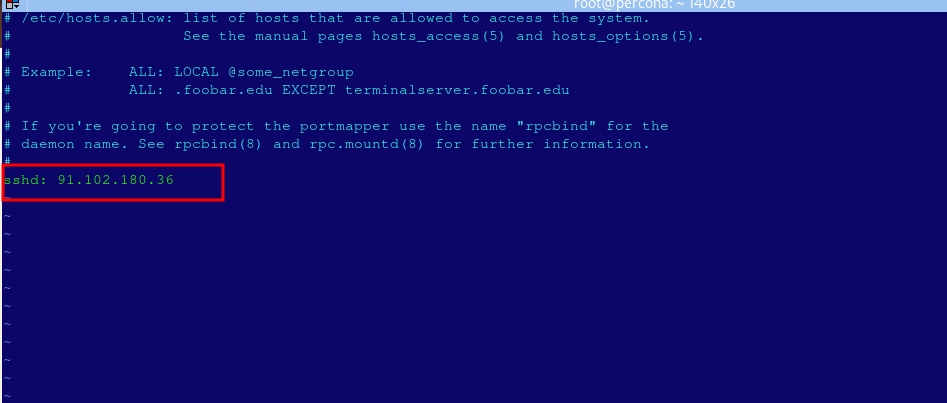
- You can allow multiple IPs by separating them with spaces:
sshd: 192.168.1.100 192.168.1.101 203.0.113.50- Alternatively, to allow an entire subnet, use CIDR notation or wildcard symbols:
sshd: 192.168.1.0/24Configure hosts.deny
Access /etc/hosts.deny,
sudo vi /etc/hosts.denydeny all other IP addresses by adding this line:
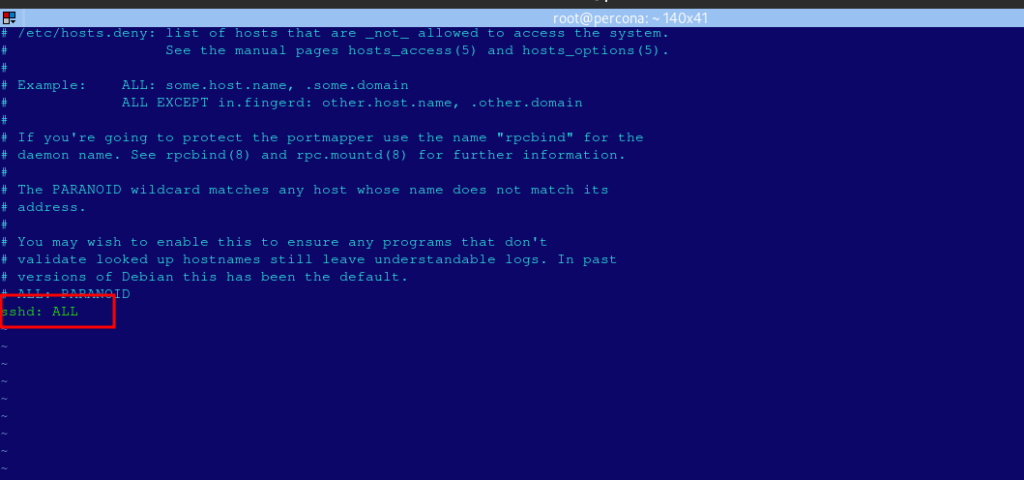
sshd: ALLThis line blocks all SSH access by default, except for those IPs explicitly allowed in hosts.allow.
Step 3: Verify TCP Wrappers Support (optional)
On some distributions, you may need to verify that TCP Wrappers is installed and supported. Install the necessary package if it’s not present:
# On RHEL-based systems
sudo yum install tcp_wrappers
# On Debian-based systems
sudo apt install tcpd
Step 4: Test the Configuration
- Once configured, test the setup by attempting to SSH from allowed and disallowed IP addresses to ensure the rules work as expected.
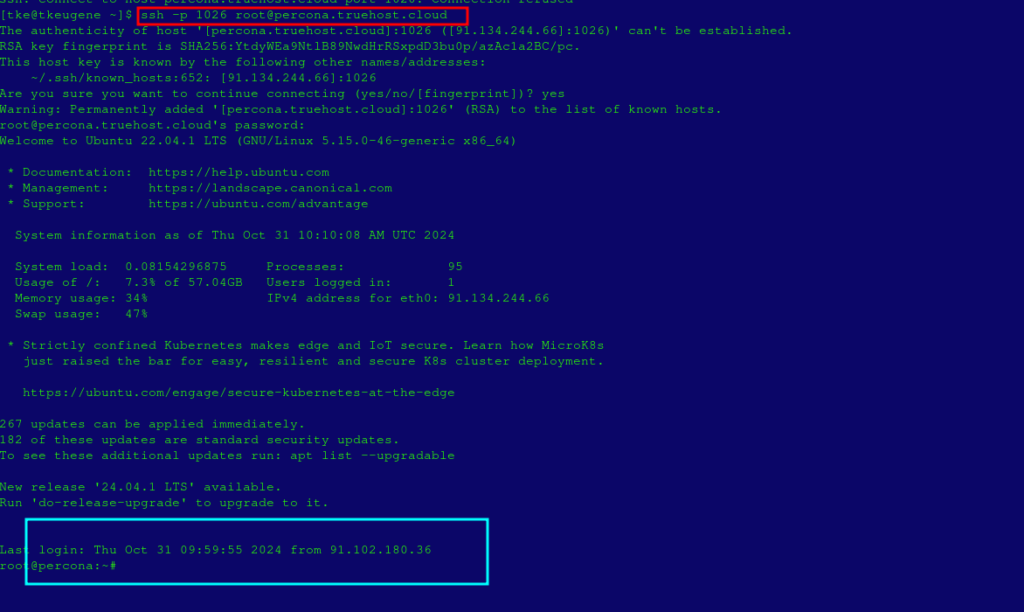
Below image shows successful connection from an allowed IP/network
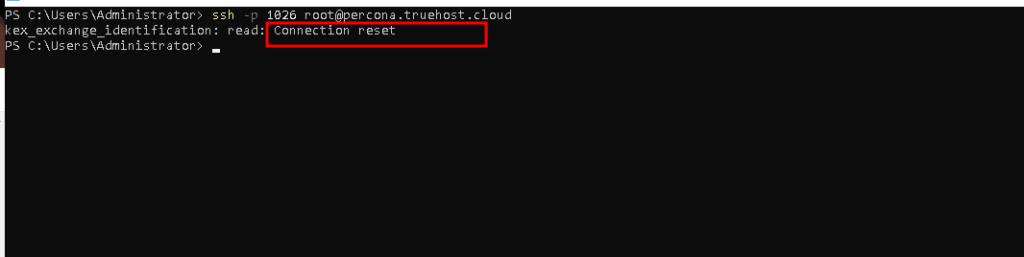
Below image shows unsuccessful connection from a denied IP/network
Example Configuration
Here’s an example of how the files might look:
/etc/hosts.allow #
sshd: 192.168.1.100 192.168.1.101 203.0.113.50/etc/hosts.deny #
sshd: ALLAuthor’s final word #
Using hosts.allow and hosts.deny is an effective way to restrict SSH access to specific IPs on Linux servers. By configuring these files, you can create a robust layer of security for your server’s SSH access, helping to protect your system from unauthorized login attempts.